As we explained in “What is VMware and why should I care?”, VMware is a type of modern virtualization that, until just a few years ago, was considered science fiction. Fully hardware-less servers now exist! In the hosting world, it’s been a game-changer. In theory, we can now have servers that never have downtime, as they’re never affected by the most common problem hosts face: computer hardware failures.
But creating a true cloud infrastructure takes more than simply using the VMware hypervisor.
And the hypervisor itself does more than just divorce servers from hardware.
Part 1: Cloud/VPS/VM exploits
The virtualization layer between your virtual server OS and the physical hardware is extremely sensitive. The right exploit in the wrong hands can allow unfettered access to all virtual servers on the hardware nodes. A cloud is only as secure as the hypervisor.
Excluding VMware (which is more popular than all other virtualization platforms combined), Xen, KVM and Virtuozzo/OpenVZ are the next most widely used hypervisors in the industry. And each of these has been affected by critical security violations that have put users at serious risk. Even the most popular non-server solution, Oracle VirtualBox (the freeware desktop computing method to create virtual machines), has had its share of vulnerabilities.
Although VMware has had some exploits – as all software does – VMware is quick to fix the issue. By contrast, Parallels/Odin is notoriously slow, and you’re at the mercy of somebody’s hobby time to fix the open-source solutions. When it comes to enterprise solutions, that’s not good enough!
VMware is the only virtualization platform that has proven to be consistently reliable year after year, in a mission-critical enterprise hosting setting. But with other platforms, major issues are an annual affair.
Example: Data takes a leak!
It was the “the Xen vulnerability that rebooted the public cloud”.
Vulnerability CVE-2014-7188 severely impacted x86 systems on the Xen virtualization platform. A VM admin was allowed to read sensitive data from the hypervisor, including data from all other VMs on the node. Without going into the technical, it was a huge memory leak that made private data public.

Some of the largest cloud providers in the world were again affected: Amazon, Rackspace, Linode and Softlayer/IBM. They had to take all servers offline in order to apply the patches. For them, the downtime was catastrophic. For customers, the downtime was a major inconvenience.
VMware was unaffected, as the threat was identified in advance.
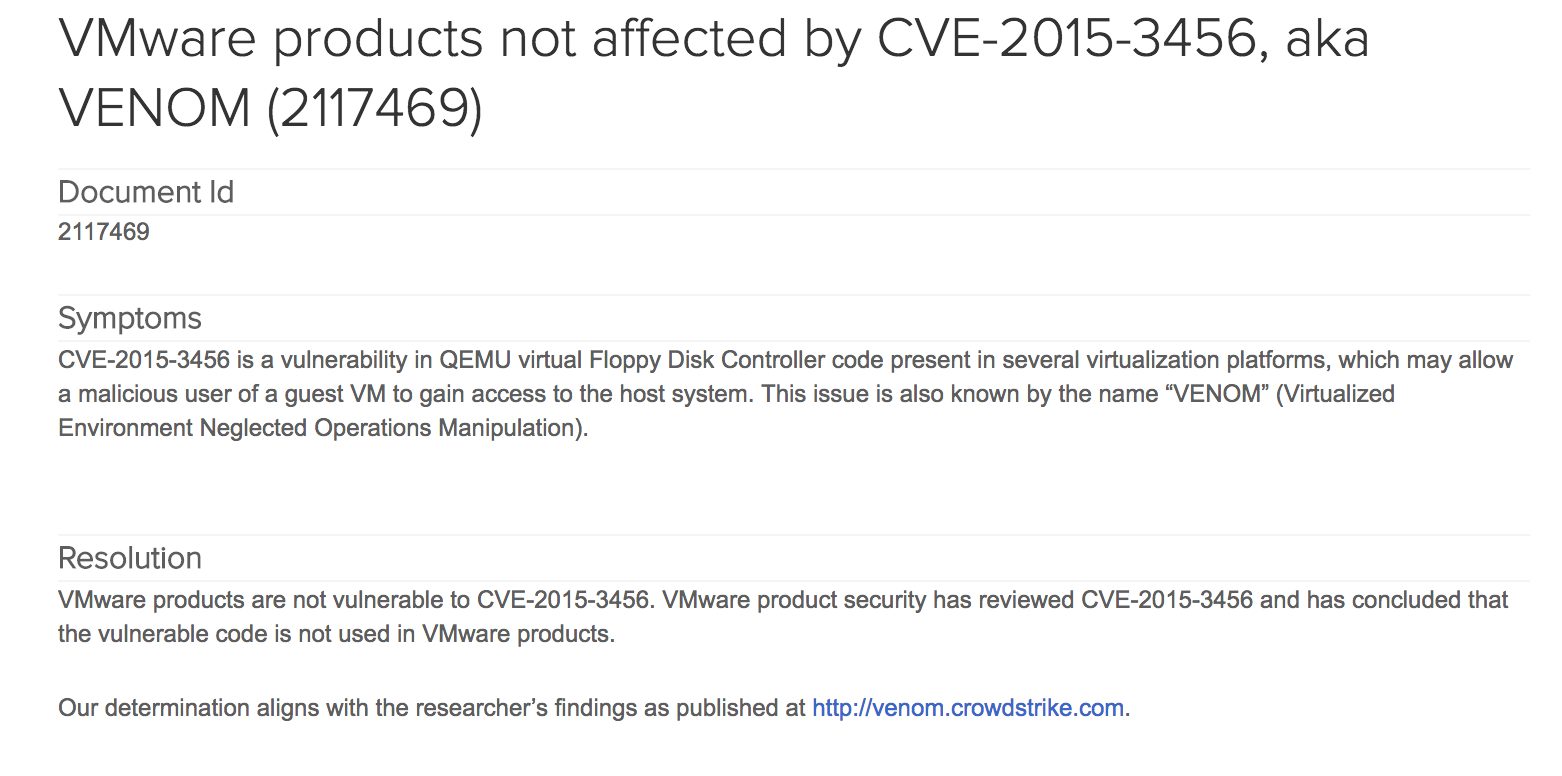
Example: VMware defeats the forces of VENOM!

No, sorry G.I. Joe fans, wrong VENOM. But it is still evil!
The “virtualized environment neglected operations manipulation” (VENOM, CVE-2015-3456) is a catastrophic security vulnerability that lies in a legacy common to most VMs. The open-source virtual floppy drive (QEMU FDC) was exploited last year. A bug in the controller could be hacked, escalated privileges for the nefarious user on any VM. The new privileges allowed complete control of the hypervisor and all VMs on the hardware node!
And many of the largest cloud providers in the world were again affected: Amazon, Rackspace, Linode and Softlayer/IBM. Once more, they had to take all servers offline in order to apply the patches.
VENOM affected both Xen and KVM environments, but VMware was not impacted. It does not contain the attack surface (virtual FDC).
Bonus: vShield Endpoint Protection
VMware includes native “endpoint protection” (anti-virus, anti-malware, network intrusive prevention) in the vSphere hypervisor suite. vShield Endpoint provides a boost in performance by running outside of the VM, at the hardware level. It results in optimal use of resources on a node. Competing hypervisors like Xen and KVM have no offloading abilities, and must run inside the virtual environment, gobbling up VM RAM and CPU to run.
Part 2: Virtual hardware stability = system security
When we talk of “security”, most people think of malware and viruses. But security is also a matter of providing a stable platform. The dictionary defines security as “the state of being free from danger or threat.” And true security is about removing or diminishing all threats.
Traditional virtualization technologies like Xen, KVM and Virtuozzo/OpenVZ truly share resources. All for one, and one for all! The VMs mingle and interact with one another, at a hardware usage level. It’s hardware fragmentation at a massive scale – not just storage, but RAM and compute as well. But VMware is different.
The Distributed Resources Scheduler (DRS) allows you group VMware hosts into a resource cluster, to segregate computing needs of the VM. What’s mine is mine, and what’s yours is yours! DRS automagically eliminates resource contention, optimizing a VM for a contiguous slice the physical server. DPS migrates VM across the hypervisor as needed. Think of it as a complex software load balancer for VMs.
DRS both monitors and makes decisions on-the-fly (though manual approval can be set).
Such things are not possible in Xen, KVM or Virtuozzo/OpenVZ.
EuroVPS = cloud host, security minded!
Cloud servers are more sophisticated compared to traditional physical server environments in almost every way. The rise of VPS and cloud computing has also given rise to hackers. Security should be a top concern of any host offering any sort of virtualized platform. Yet some of the top cloud companies in the world have been caught with their pants down.

While it is impossible to fully eradicate the risk of security threats associated with cloud server platforms, you can minimize the potential vulnerabilities by opting for a hypervisor that has a solid reputation for being secure. In other words, VMware.
At EuroVPS, we offer premium VMware cloud/VPS services that is highly secured, ensuring that your websites are always online.
Investing in a mature virtualization technology is the most fundamental, yet highly effective measure, to prevent visitors with malicious intent from gaining access your cloud server. It’s not a cheap setup, but that’s what we have. And we want you to have it to. Is your business that important? Ours is.
Footnote: Realize that “cloud” is not a type of server, but an infrastructure. Clouds still power shared hosting and virtual servers. VPS is a virtual server. So in this blog, we’ll refer to “cloud servers” as VPS or “virtual servers” or “virtual machines” (VM) interchangeably. It is the same.